Transport Layer Security (TLS)
The Transport Layer Security (TLS) protocol, previously known as Secure Sockets Layer (SSL), is used in conjunction with HTTP to secure data that is transmitted over the Internet, specifically the World Wide Web, converting it to what we refer to as the HTTPS protocol.
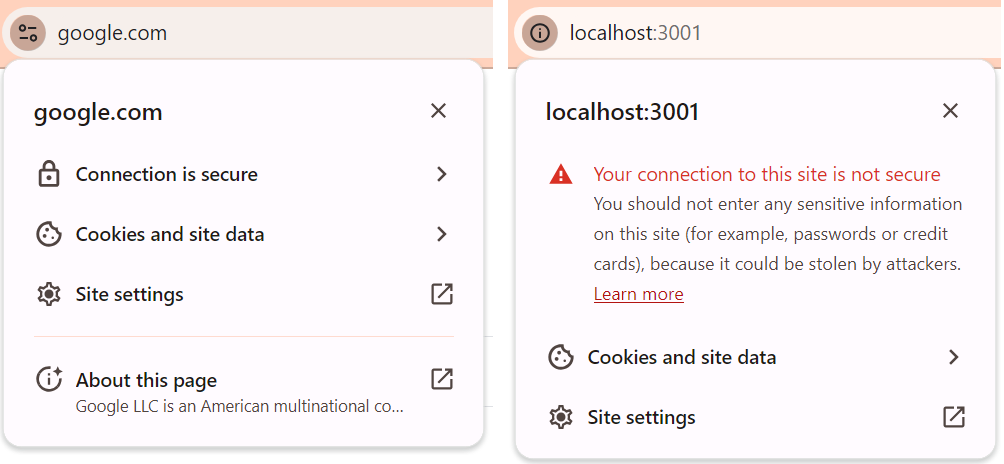
When you visit a website using your browser you get an indication of whether or not the website you are connecting to is using TLS or an open connection (which is not safe).
See below for the indicators on Google Chrome:
How does TLS work?
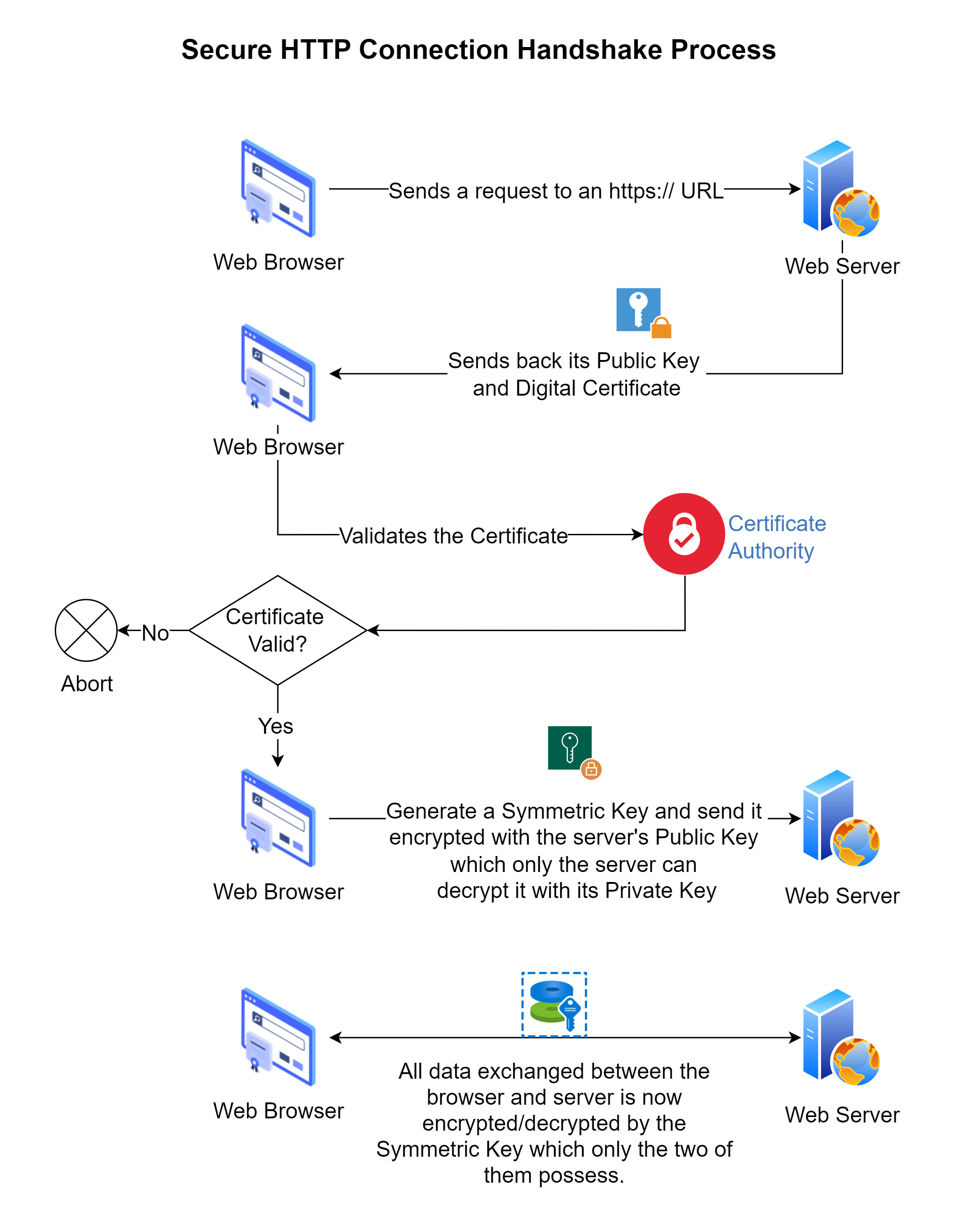
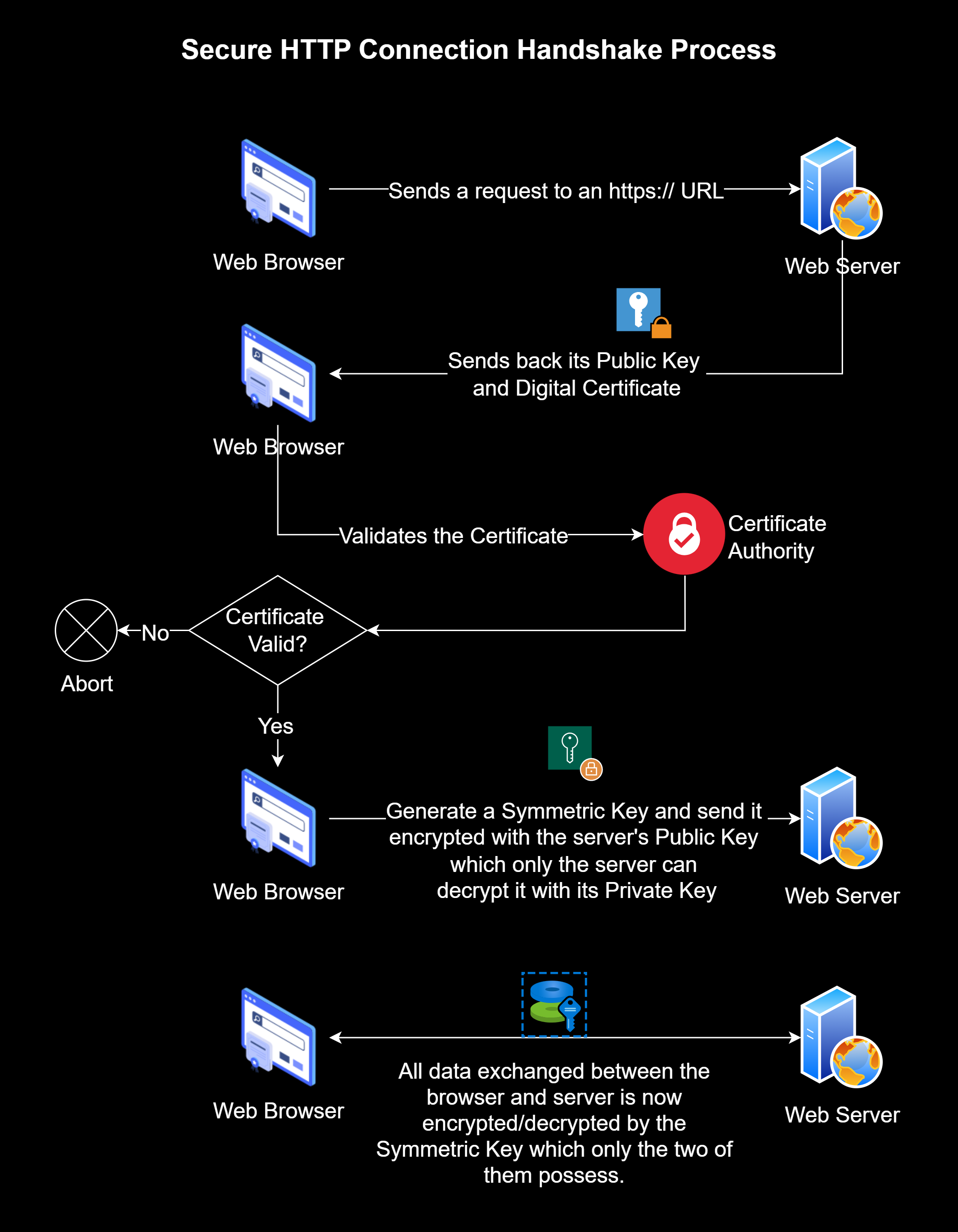
TLS uses a combination of both symmetric and asymmetric encryption. It executes a process known as a handshake between the client and server to establish a two-way secure connection for data exchange. While the process is quite complex, the concept is easy to understand.
Consider the example of an online banking transaction. Customers, using their web browser as the client, will connect to the web server managed by the bank. The following steps are executed to establish a secure connection:
-
The web browser (client) first needs to confirm that the bank web server is legitimate. For this, the server sends to the client something known as a Digital Certificate. Digital Certificates are issued to businesses by a globally certified Certification Authority (CA) to confirm that their web servers are legitimate and can be trusted. The client verifies the digital certificate (by connecting with the CA) and can ensure that the bank server is legitimate.
-
When issuing the digital certificate to a business, the CA also generates and issues a private-public key pair. The business keeps the private key on the server, but sends the public key to any client that wishes to connect to it.
-
Once it has been confirmed that the bank server is legitimate, the client generates a symmetric key. It encrypts the symmetric key with the public key received from the server and sends it to the server. Since the data can only be decrypted with the private key, which is only known to the server, nobody else can access the symmetric key.
-
Once the server receives the encrypted symmetric key, it decrypts it with its private key and extracts the symmetric key. Now both the client and the server have a copy of the symmetric key.
-
From this point on, for the duration of the session, the client and server will both encrypt data using the symmetric key before sending it across so that the data exchange is secure and cannot be read by anyone else, even if it is intercepted.