Encryption
Digital data, by default, is captured, transmitted accross networks, and stored in databases in plain text, that can be easily read and understood by a human. For public and inconsequential data this is not a concern. But for private, confidential, personal, and sensitive data, this can be a major concern since if the data falls into the wrong hands it could result in financial and reputational damage to an individual or a business.
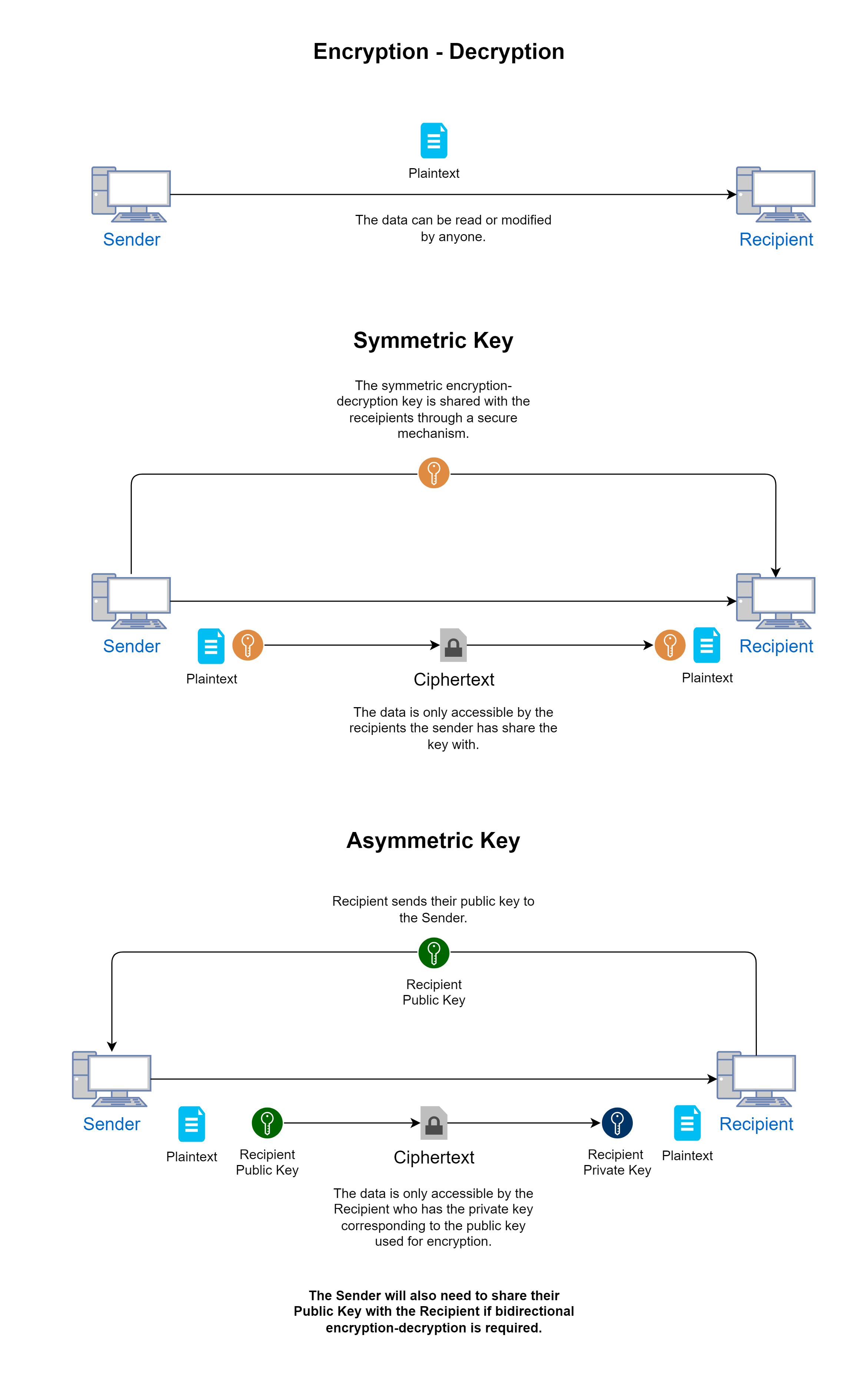
Cryptography is the study and practice of techniques and mechanisms to secure digital data such that it can only be viewed and modified by the owner of the data or by entities trusted and authorized by the user. The two main steps in this process are encryption and decryption. Encryption is the process of converting plaintext to secure text (also referred to as ciphertext), and decryption is the reverse process of converting ciphertext to plaintext.
Encryption is required wherever data is to be shared or stored in a manner that is accessible by a possible adversarial entity with malicious intent. In our current context, the focus will be on the encryption of data exchanged between systems over the Internet, a public network accessible to everyone, or stored in a database. But in reality, encryption could be required for a confidential phone conversation (voice encryption as it travels over the public phone line) or even for a written document couriered from one place to another through a public delivery system.
Objectives of Encryption
Encryption of data has multiple objectives, the two most notable ones being:
- Data Confidentiality:
One of the reasons hackers try to access data is to use confidential information for their benefit. For example, when a customer is making an online purchase he or she enters credit card information. If a hacker were to access that information, the hacker could use it to make online purchases for themselves, while the original credit card holder will get billed for the transactions. In such a hack, the data is read by the hacker but allowed to be received by the recipient as well without any tampering with the data.
This aspect of data security, where data being shared by one entity to another should not be readable by any entity, is referred to as Data Confidentiality.
- Data Integrity:
Another option for hackers is to intercept the data being transmitted, make some changes to that data, and then send the modified version to the recipient. To take the same example of online shopping, the hacker may not steal the credit card information but may change the shipping address. The purchased products will then be shipped to the hacker's address while the original buyer will be billed for the transaction. In a banking transaction, the amount or the recipient account number may be modified. The transaction will go through, but the wrong account or amount will be credited.
This aspect of data security, where the recipient is guaranteed that the data received is exactly as it was sent by the sender, is known as Data Integrity.
Encryption Algorithms
Encryption and decryption of data are achieved by a complex algorithm and what are known as keys. Keys are random strings of bytes designed to work with the algorithms. Keys are usually long and unpredictable. The longer the key, the harder it is to crack the encryption code. There are many algorithms, each with its strengths and limitations. Some common ones are Data Encryption Standard (Triple DES), Rivest–Shamir–Adleman (RSA), and Advanced Encryption Standard (AES).
The algorithms are extremely complex, and only a handful of companies can implement them. Almost all other application owners will buy and use products that implement these algorithms.
There are two kinds of encryption mechanisms:
- Symmetric-Key Encryption:
In the symmetric-key mechanism, the same key is used to encrypt and decrypt the data. Either the sender or the receiver can generate the key and share it with the other. Once both the sender and the receiver have the key, they can encrypt and decrypt the data using that key and be assured that nobody else will be able to view or modify the data without the key. This mechanism works where the sender and receiver know each other in advance and have the trust and a secure mechanism to share the key with each other.
- Asymmetric-Key Encryption:
In the asymmetric-key mechanism, two keys (referred to as a key pair) are used, where one is referred to as the private key and the other as the public key. When data is encrypted using the public key, it can only be decrypted using the corresponding private key and vice versa. This mechanism is used where only one-way encryption is required. For example, a business may share its public key with all its customers, while keeping the private key to itself. Any time a customer wants to send data securely to the business, it encrypts it with the public key received from the business. The data can be decrypted only with the private key, which is only with the business.